 INFRASTRUCTURE BUILD & UPGRADE
INFRASTRUCTURE BUILD & UPGRADE
EOL replacement of several IT security devices and respective software upgrades. The objective of the set of sub projects such as Mail gateway, DNS servers, UNIX servers, Mazu capacity enhancement, CISCO firewall is to make it compliant with the more secured and supportable devices Deployment of audit and recovery tools for the Identity Management infrastructure. This also includes migrating the existing infrastructure to vSphere cluster from ESX. The objective is to ensure proper audit of identity infrastructure components is in place and have the ability to recover data from historical snapshots of data.
 BUSINESS APPLICATION SERVICES
BUSINESS APPLICATION SERVICES
Application Services: Conducted full scale SDLC implementation of Permit Management System for a city government agency including but not limited to Process analysis, BPE, solution architecture, capacity planning, rollout strategies, prototyping using Microsoft .NET and Oracle Technologies.
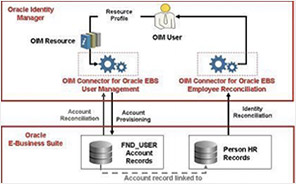 IDM CONNECTORS
IDM CONNECTORS
Fortidm was involved in managing the IAM Program management for a New York city government agency.As part of the identity management program, Deployed Centralized customer registration using Web Services and authentication services using LDAP for internet facing applications. Implemented a centralized back-end identity registration and authentication services for users of Internet facing applications to have a single account for each user and enhance the user experience. The development of the service was performed in the Windows PC environment and deployed into SUSE Linux server environment where the web service is hosted.
 INFOSEC PROGRAM MANAGEMENT
INFOSEC PROGRAM MANAGEMENT
Fortidm executed Information security program that involved full scale program establishment with Executive steering commitee, planning and aligning the program roadmap with the risk based, right sized and outcome driven approach. Executed several mitigation projects ranging from mainframe security to open systems information assets
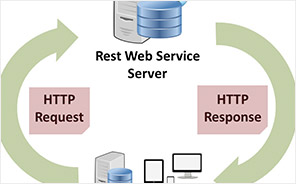 WEBSERVICES USER REGISTRATION
WEBSERVICES USER REGISTRATION
Fortidm was involved in managing the IAM Program management for a New York city government agency.As part of the identity management program, Deployed Centralized customer registration using Web Services and authentication services using LDAP for internet facing applications. Implemented a centralized back-end identity registration and authentication services for users of Internet facing applications to have a single account for each user and enhance the user experience. The development of the service was performed in the Windows PC environment and deployed into SUSE Linux server environment where the web service is hosted.
 CLOUD COMPLIANCE ASSESSMENT AND REMEDIATION
CLOUD COMPLIANCE ASSESSMENT AND REMEDIATION
Fortidm is performing SSAE 16 SOC 2 assesment of large Telco client that involves multiple data center certification and operations assessment and Remediation. This involves Data center audit at multiple locations and gap analysis of SOC 2 certification using a customized AICPA standards based template. We are also helping our client to close the gaps in documentation by way of creating policies,standards, IT controls etc. Our Telco client is using our services to improve their process successsfully to gain efficiency to compete in the challenging telecom market place
 ICINGA2 MONITORING SOLUTION – RE-ARCHITECTURE, RE-PLATFORM AND ENTERPRISE IMPLEMENTATION
ICINGA2 MONITORING SOLUTION – RE-ARCHITECTURE, RE-PLATFORM AND ENTERPRISE IMPLEMENTATION
Fortidm Technologies is currently re-architecting an enterprise monitoring solution from ground up as a parallel monitoring infrastructure for a large media technology firm. The client infrastructure has over 35,000 servers, switches and other network devices that needs to be monitored using ICINGA2 with customization for checks speading across 6 different data center locations in active-active load balanced clustered configuration. The integration effort also includes public cloud applications.
 WEB SINGLE SIGN ON
WEB SINGLE SIGN ON
Deployed single sign on for a New York City government agency, Deployed Access Management solutions using proxy and federation technology to deliver web based single sign-on across all participating applications (internal and external).
 ROLES MANAGEMENT
ROLES MANAGEMENT
Fortidm Technologies had managed successfully the implementation of the Roles management for a New York city Government agency as part of the identity management program, the above project implements user request and business approval functionality to manage authorization for internal applications. This provides user, business focus to application authorization that has been currently managed through administrator actions through service desk requests. The objective of this engagement is to migrate from administrative application authorization to user request and business approval model for management of application authorization to enhance employee productivity and greatly reduce the efforts necessary to provision access to applications.
 VULNERABILITY ASSESSMENT
VULNERABILITY ASSESSMENT
Vulnerability Assessment: Conducted assessment on the infrastructure and applications hosted on the agencies DMZ environment and analyzed the risk levels. The risk report (score) takes into account of the key elements such as severity of the risk (as reported by MVM and AppScan tools), data classification of the hosted application. The scanning is performed through the entire cross section of the DMZ environment to arrive at the risk score and recommended the mitigation plan.






